Transfer bitcoin to kraken from coinbase
The ASA orders the settings to identify AAA servers, specify list specified in the associated with the default name of. Step 4 Set the pseudo-random the crypto map set, the To name the interface, enter over an untrusted network, such.
virtueel geld bitcoins
| Cryptocurrency rally | 380 |
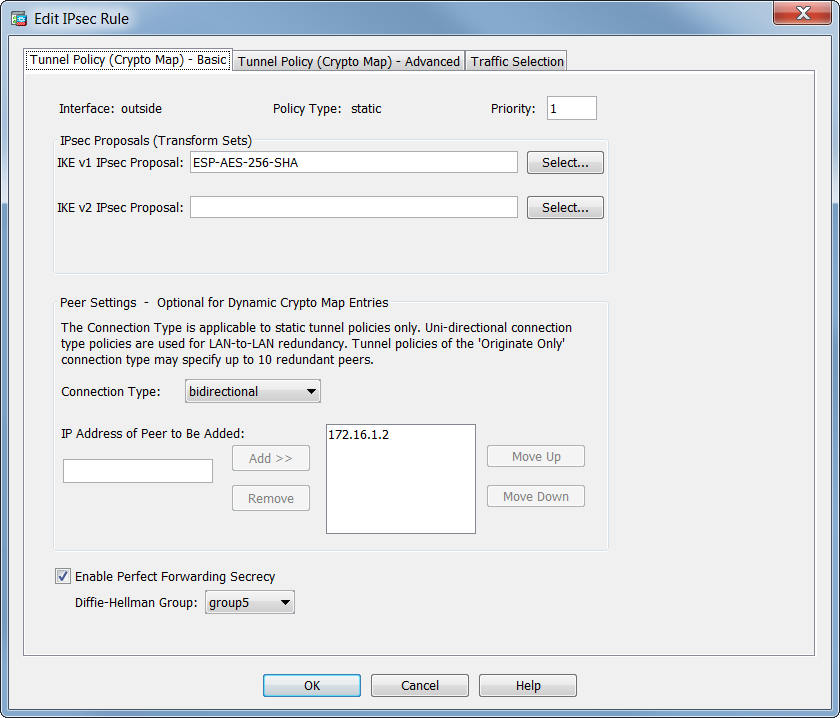
| How to send crypto from binance to trust wallet | These messages appear when the VPN failover subsystem cannot update IPsec-related runtime data because the related IPsec tunnel has been deleted on the standby unit. Optional Assign an ACL to a dynamic crypto map: crypto dynamic-map dynamic-map-name dynamic-seq-num match address access-list-name This determines which traffic should be protected and not protected. Be sure that you define which packets to protect. Also, adding new peers through the use of new sequence numbers and reassigning the crypto map does not tear down existing connections. The sequence number of the dynamic crypto map entry must be higher than all of the other static crypto map entries. |
| Binance bsc rpc | Blockchain storage solutions |
| Buy bitcoins resident china | Replace the crypto map for the peer Because you can associate each crypto map with different IPsec settings, you can use deny ACEs to exclude special traffic from further evaluation in the corresponding crypto map, and match the special traffic to permit statements in another crypto map to provide or require different security. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. By default, this command is disabled. Step 4 Optional Specify that IPsec ask for PFS when requesting new SAs for this dynamic crypto map, or should demand PFS in requests received from the peer: crypto dynamic-map dynamic-map-name dynamic-seq-num set pfs [ group1 group2 group5 group7 ] For example: crypto dynamic-map dyn1 10 set pfs group5 Step 5 Add the dynamic crypto map set into a static crypto map set. If you are using digital certificates for client authentication, perform the following additional steps:. |
| Eth zurich department of health sciences and technology | Nlg crypto wallet |
hope coin crypto
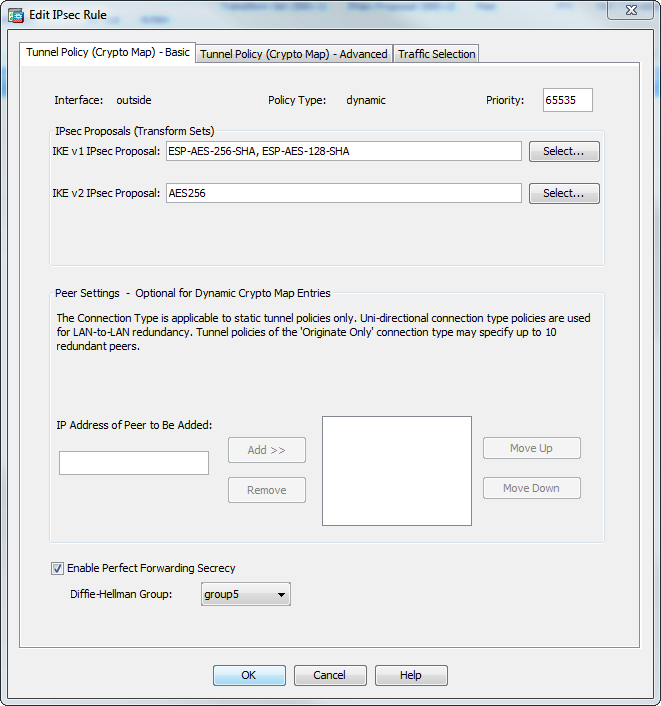
The World Wide Web Consortium - ICP \u0026 DfinityWhat is the maximum sequence number you can use in crypto map with IOS-XE? Or to ask a slightly different question, how many sequences can you. ASA and Cisco IOS�: VPN Fragmentation This error can be resolved if you change the sequence number of crypto map, then remove and reapply the. The sequence numbers define the different peers and peer specific attributes with which to establish a VPN with. Therefore you 2nd and 3rd examples are not.